This is a written assignment for Noroff University on the EternalBlue exploit.
Introduction
EternalBlue is an exploit, developed by the National Security Agency (NSA). It was leaked by a hacker group known as the Shadow Brokers on April 14th, 2017. The exploit was one of over twenty professional and advanced hacking tools leaked. It exploited a zero-day vulnerability in almost every Windows version prior to Windows 8, a flaw in the Server Message Block (SMB). The exploit allows for privilege escalation, lateral movement, and arbitrary code execution on vulnerable machines.
EternalBlue exploits a memory overflow in the srv2.sys driver in the SMB protocol, specifically a Non-Paged Pool overflow. It accomplishes this through a malformed header in the NT Trans2 packet header. The malformed header includes a pointer that points to the section of memory that holds the embedded shell-code, and by gaining control of the execution flow of the srv2.sys driver, the exploit is able to redirect it to the embedded shell-code that allows for the execution of the payload.
The Shadow Broker Leak
The Shadow Brokers is a hacker group that attempted to auction off what they claimed to be NSA cyber weapons, developed and used by the NSA,. Specifically they attributed the tools to the Equation Group, a highly sophisticated APT likely operating under the command of the Tailored Access Operations (TAO) unit of the NSA. After failing to gain the desired effect from the auction, the group released the tools for free. The tools released included advanced and sophisticated exploits and backdoors such as the EternalBlue exploit covered here, and the DouplePulsar backdoor. The identity of the Shadow Brokers remain questionable, primarily due to motives. Edawrd Snowden, like many, heavily suspect Russian agents to be behind the leak but some dispute this due to the value these tools would have for Russia if they were to remain secret. This viewpoint is reinforced by the fact that the WannaCry attacks struck earlier than the later Russian attributed NotPetya attack, which could indicate the Russian agents of the GRU had not had access to these tools earlier than other APT groups. Some have speculated this leak was an insider threat
While the vulnerability was a zero-day when the NSA was utilising it, it was not when the exploit actually leaked. The NSA had secretly informed Microsoft about the exploit, and they had patched it about a month prior to the leak (WashPost). The exploit would nonetheless go on to be utilised in several cyber operations, with two of particular note. Only a month after the leak, on the 12th of May 2017, the WannaCry ransomware worm affected over 300 000 computer spread across 150 nations, and was attributed to the North Korean APT The Lazarus Group by the US. Then another month later, on June 27th, the NotPetya wiper-ware masquerading as ransomware went worldwide and caused the most damaging cyber operation yet, with estimated costs of over 10 billion usd. This operation was later attributed to the Russian GRU, the group known as Sandworm specifically.
SMBv1
The Server Message Block is a protocol that allow atomic read and write operations between a client and a server, and is implemented in Microsoft Windows. The protocol operates on the Application layer, and at times in the Presentation layer (using the OSI model), and commonly relies on NetBIOS as a protocol for the transport layer using TCP/IP. It relies on data packets, each containing a request or response from the server. SMBv1 had several design limitations and security vulnerabilities. An SMB packet consists primarily of an SMB header and a SMB payload, containing the actual data being transferred. The packets are known as NT Trans packets, and are the data transfer packets that are created after the session is established. When the data in the message exceeds the size determined by the value of SMB MaxBufferSize, the protocol splits the packets into multiple. These secondary packets are called NT Trans2 packets, and encompass any further data unable to fit in the first packet.
EternalBlue exploits a vulnerability denoted as CVE-2017-0144. The vulnerability occurs due to a race condition that occurs when SMBv1 handles specially crafted SMB packets and allows for arbitrary code execution with system-level privileges. The vulnerability lies in the srv2.sys kernel driver.
CVE-2017-0144
The srv2.sys driver is a critical component in the SMB protocol, and suffered from inadequate memory permission checks and kernel isolation in the Windows OS. This left the driver vulnerable to be exploited by EternalBlue and allowed for arbitrary code execution.
Memory permission checks are security measures that ensure and enforce privileges for memory access upon processes, applications, or components. They are enforce both by the OS and hardware. Memory permission checks ensure processes with lower privilege don’t read or write on data of a higher privilege, and ensures systems stability and security. In the CVE-2017-0144 vulnerability, the srv2.sys driver failed to perform such checks and did not validate SMB packets, which left the driver vulnerable to a buffer overflow.
A buffer overflow is a common software vulnerability that occurs when a program attempts to write more data to a fixed size block of memory (buffer) than it can hold. The additional data can then overflow and overwrite or replace data in adjacent buffers. These vulnerabilities occur in two places, the stack and the heap. These to primary memory regions manage memory allocation. The stack holds variables, function call information, and local memory allocation and has a fixed size, while the heap handles memory allocation for objects that extend beyond a single function call and is dynamic in size and nature.
Exploiting Race Conditions
The race condition occurs as the srv2.sys driver uses multiple threads to process incoming packets, and the attacker can therefore send multiple crafted packets to increase the chance of triggering the vulnerability. The goal of the attacker is to take control of the execution flow of the driver and execute arbitrary code on the system.
Due to the srv2.sys driver failing to adequately validate the incoming SMB packets an attacker can craft malformed packets containing incorrect size values, which causes the driver to improperly allocate memory when processing the packet. Due to the incorrect size value of the crafted package, the driver allocates a smaller buffer than required causing a buffer overflow when the driver copies data from the packet to load into the allocated buffer.
When the buffer overflow occurs, the attacker is aiming to adjacent kernel memory structures. In particular, aiming for blocks that handle the Non-Paged Pool (NPP) memory. The NPP is a region of memory that holds key objects crucial for system stability and operation. These objects include kernel objects. The packet is crafted to gain control of kernel memory.
With this memory control, the attacker can modify pointers to redirect the flow of execution from the driver to their own malicious code stored in the crafted packet. This is typically a shell-code or a payload granting access to the target system, such as the DoublePulsar backdoor (also developed by the NSA, and released in the same leak). At this point the attacker would have gained control of the system and can execute code.
EternalBlue Function
The key to EternalBlue’s functioning is the Windows function in SMB called **srv!SrvOS2FeaListSizeToNt. **The function deals with the transfer between different file systems, here specifically the OS/2 and Windows NT file system. It calculates the needed size of memory to hold a NT File Extended Attribute (FEA) list structure when given an OS/2 FEA file structure. The function operates as follows:
- The input is a OS/2 FEA list structure
- The function iterates through the list structure
- The function calculates the needed memory to hold the matching NT FEA structure, given the current OS/2 structure
- The function returns the total needed size of memory to store the entire NT structure
However, there is a mathematical error in the function that EternalBlue exploits. The mathematical error causes an integer overflow due to a miscalculation, and causes the function to return a lower value than is needed and causing less than required memory to be allocated leading to a buffer overflow.
The buffer overflow can be achieved using another bug in SMB. This next bug occurs in the two subcommands SMB_COM_TRANSACTION2 and SMB_COM_NT_TRANSACT. These commands both have _SECONDARY commands, that are used when the data sent is unable to fit on a single packet. The difference in these two commands are the packet sizes. NT_TRANSACT requires a data packet twice the size of TRANSACTION2. When a client sends a NT_TRANSACT subcommand, then immediately sends a TRANSACTION2 subcommand the protocol fails to adequately validate the change in expected packet size and allocates the memory needed for the TRANSACTION2 command, which is inadequate for the NT_TRANSACT command it is actually allocating memory to. While the protocol understands it is receiving two subcommands, it nonetheless assigns memory to both packets using the information from the last one it receives, and as the TRANSACTION2 packet is that packet, and said packet is smaller than the NT_TRANSACT packet, the NT_TRANSACT packet is assigned too little memory, causing the overflow.
Finally, a third bug in SMB enables heap spraying to be used. Heap spraying, much like buffer overflows, exploit memory management. While a buffer overflow writes more data to memory than the memory can handle in order to break out into memory segments, heap spraying is more targeted and inserts data into specific memory segments. The idea is to insert code into memory that can then be pointed to and run. An issue that can arise using this technique is when the computer begins to read the code from the middle, becoming confused and often crashing. This is avoided by using NOPs, or No Operation. NOPs are machine level instructions that, as the name suggests, do no operation. Were the computer to begin reading in the middle of the code, it would pass through the NOPs until reaching the intended code to be run. If the heap spray is successful, the attacker is able to write and execute their shell-code and from here gain control of the system and deploy her payload.
Example
This example was run from source machine (192.168.56.1) against target VM (192.168.56.101). The target is a VM running darksec’s Windows Server scenario, as supplied through the ExploitationWorkshop by NorOff.
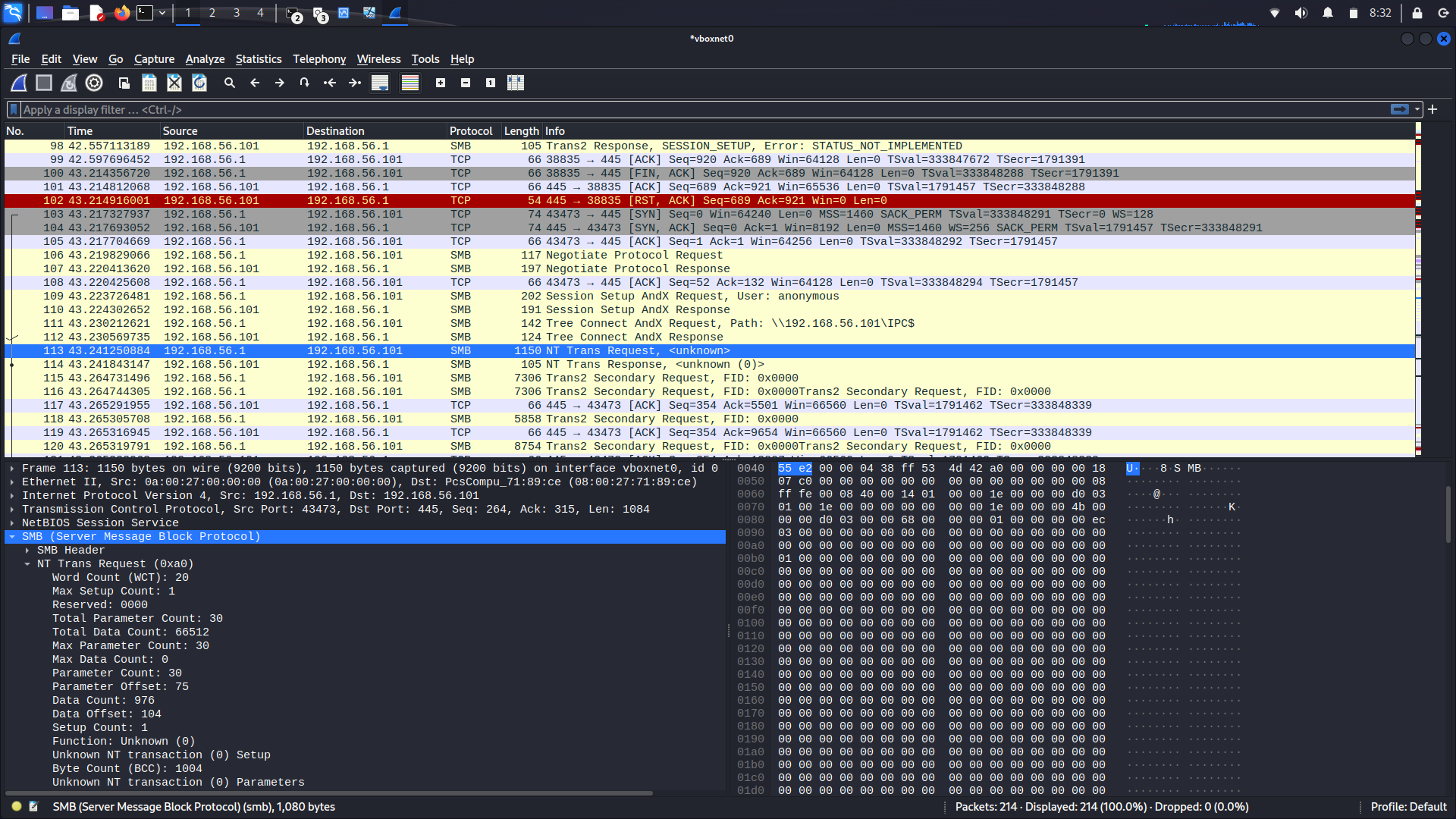
Note, in Figure 1, the NT Trans request with a large Total Data Count, and the packet being filled with zero values to pad the size. This precipitates several NT Trans2 packets to follow, and the Trans2 Secondary request sent immediately after to trigger the buffer overflow as described earlier.
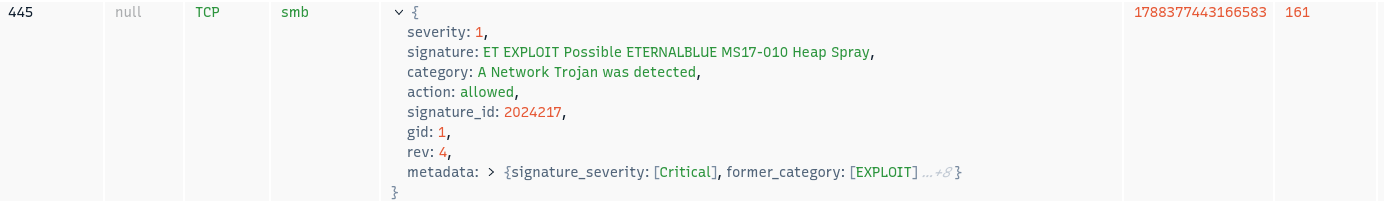
In Figure 2, Zui has detected in packet 161 the heap spray technique
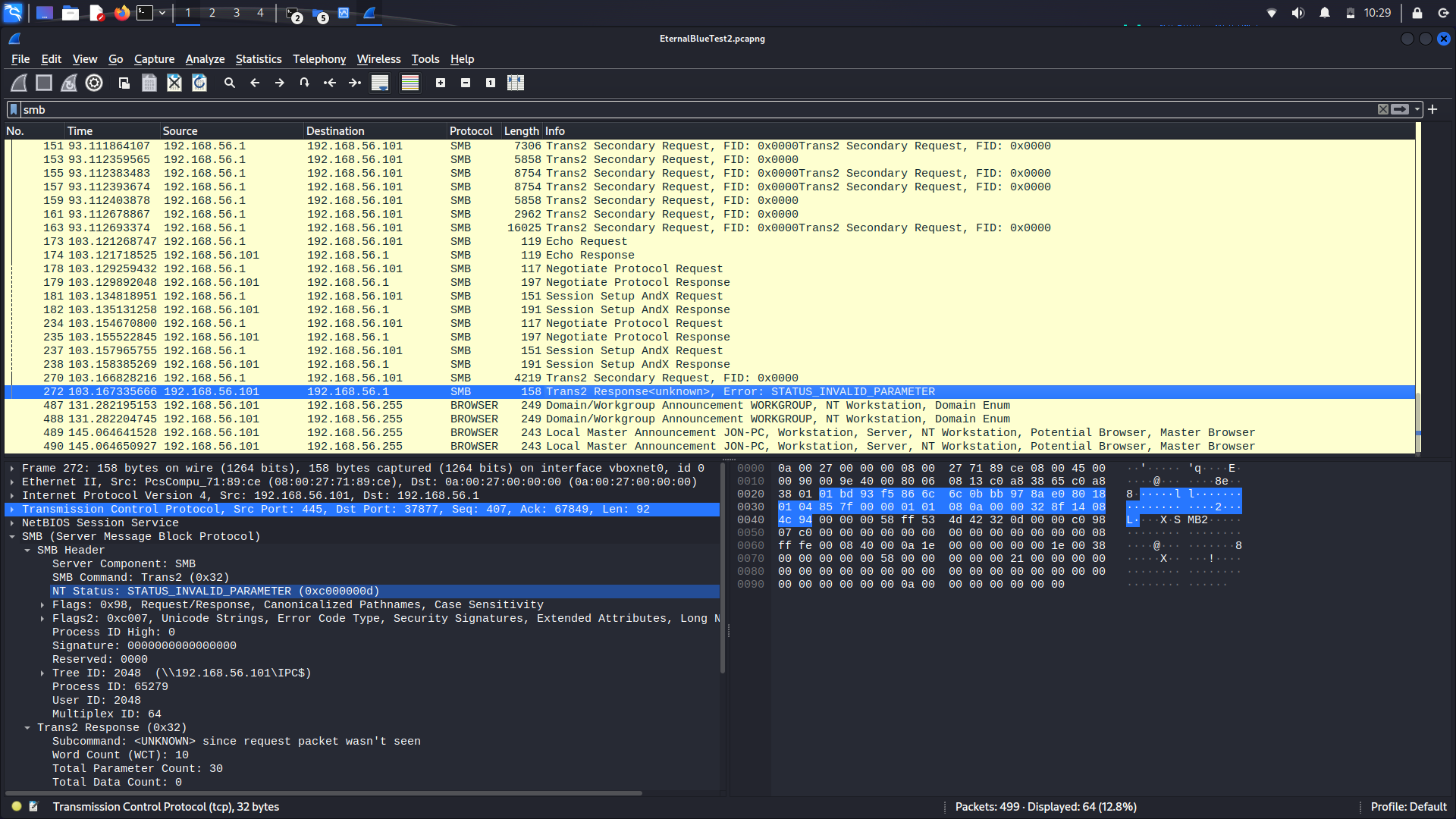
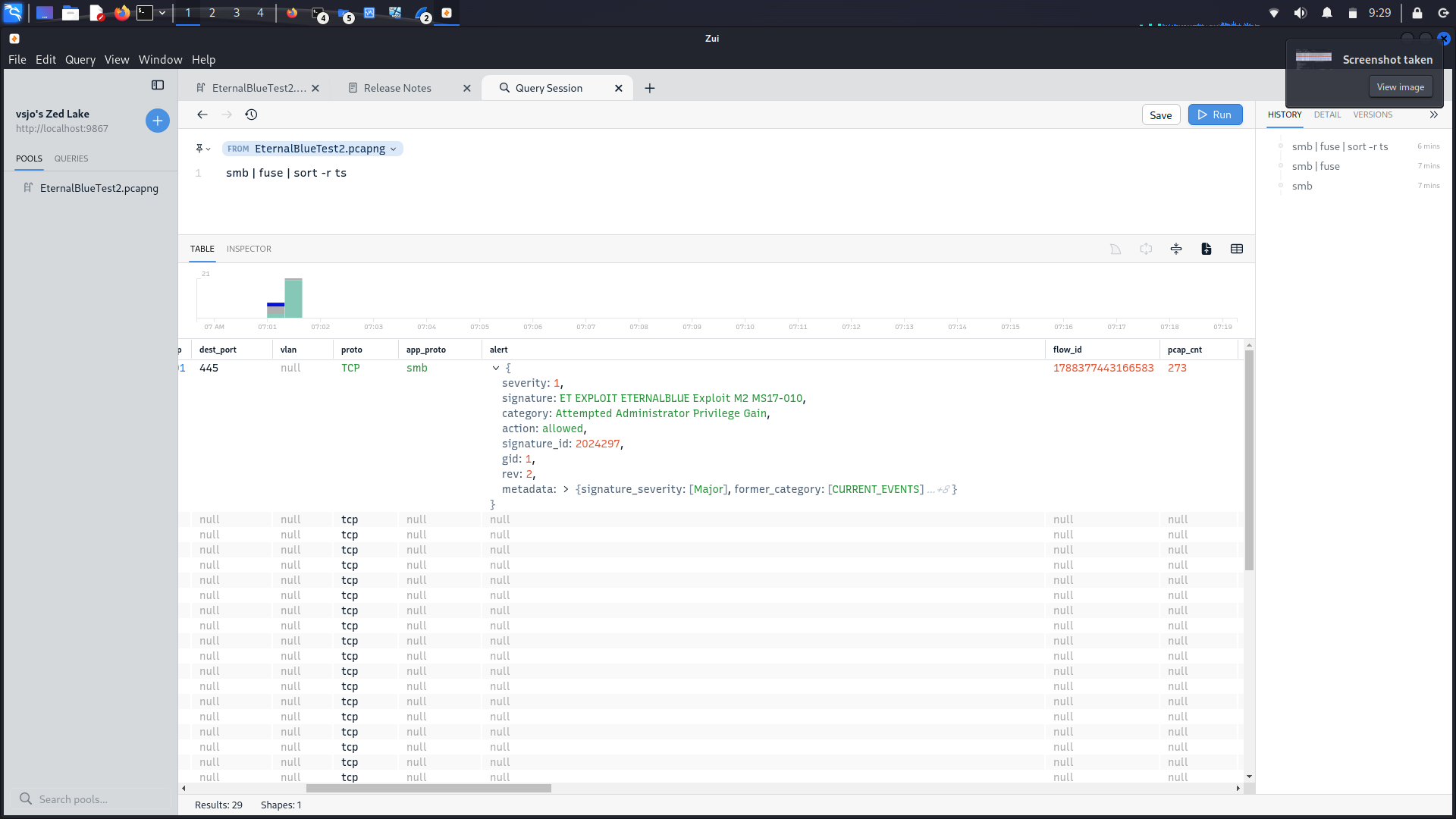
In Figure 3, the victim responds with the error STATUS_INVALID_PARAMETER, indicating that the crafted message has indeed successfully caused the system to behave unexpectedly, and likely means the overwrite attempt has been successful. This is further evidenced by analysing the packets using Zui (Figure 4). It detects the EternalBlue exploit seemingly attempting to gain administrator privileges in Packet 273, following the STATUS_INVALID_PARAMETER in packet 272.
Conclusion
EternalBlue is a notorious exploit with severe consequences, as would be expected by the tools developed by advanced and professional agencies such as the NSA. These tools being leaked by The Shadow Brokers has caused massive challenges within cyber security, and was instrumental in key cyber operations such as WannaCry and the devastating NotPetya pandemic of 2017. The fact that the NSA informed Microsoft about their discovered and exploited zero-day meant EternalBlue was not in fact exploiting a Zero Day when it began to emerge, yet failure to adequately patch and update systems meant the patch was limited in its effect despite its availability. This exploit further goes to show the inherent dangers of failing to disable or relying on outdated and vulnerable protocols such as SMBv1. EternalBlue stands as a famous example of the active roles governments and their agencies have begun to play in the cyber security world, while further reinforcing the need for strong security measures and a culture of digital expertise where security is prioritised and given significant consideration.

iptv smarters pro
It’s a shame you don’t have a donate button! I’d definitely donate to this outstanding blog! I guess for now i’ll settle for book-marking and adding your RSS feed to my Google account. I look forward to brand new updates and will share this site with my Facebook group. Chat soon!
mxl tv
Hey! I’m at work surfing around your blog from my new apple iphone! Just wanted to say I love reading through your blog and look forward to all your posts! Carry on the outstanding work!