This was an assessment written for Noroff University, doing network analysis and threat hunting
Network Context:
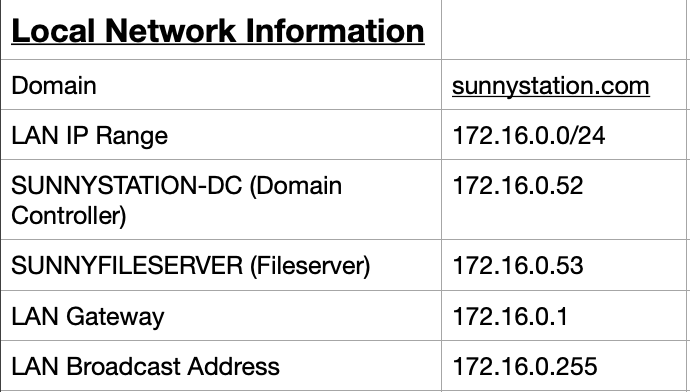
Figure 1.1.1 – Network Context
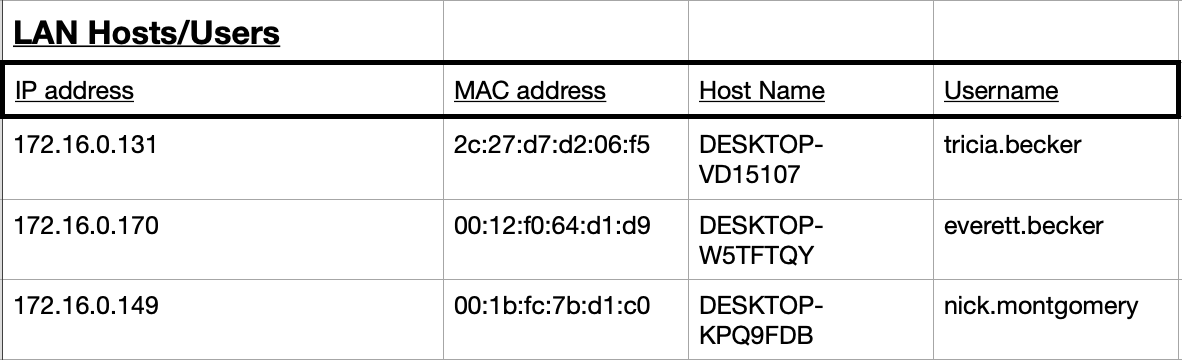
Figure 1.1.2 – Identified Hosts
This report is an analysis of a network capture from the local netwrok 172.16.0.0/24, on behalf of Sunny Station. The report is primarily an analysis of a provided .pcap capture file of the network. The data captured covers the timespan between April 8, 2022 at 18:22 to 19:07. The intent is to discover suspected malware causing degradation of the network.
Most networks use DHCP to give endpoints their IP, and services like NBNS. Filtering for NBNS requests and seperately filtering for udp traffic on port 67 (used by DHCP servers) to identify the local hosts on the network. With the host IP, the remaining information on the hosts was found by filtering on IP and tcp.port== 445 to find Host name, MAC addresses and usernames for the host. The gathered information is viewed in figure 1.2. There are three identified hosts.
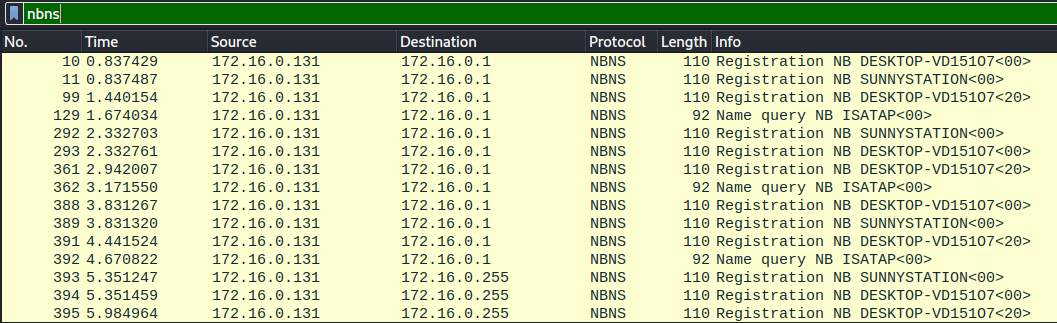
Figure 1.1.3 – NBNS Traffic
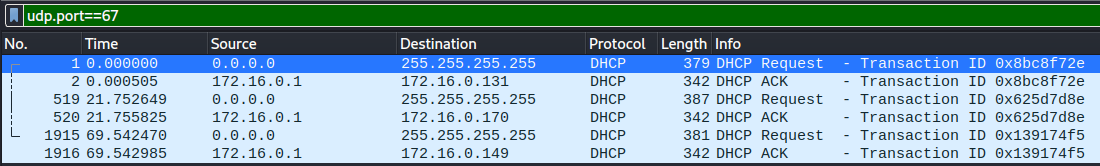
Figure 1.1.4 – DHCP Requests
The hosts on the local network are 172.16.0.131, 172.16.0.149 and 172.16.0.170. The users of these hosts are, in order, Tricia Becker, Everett Becker and Nick Montgomery.
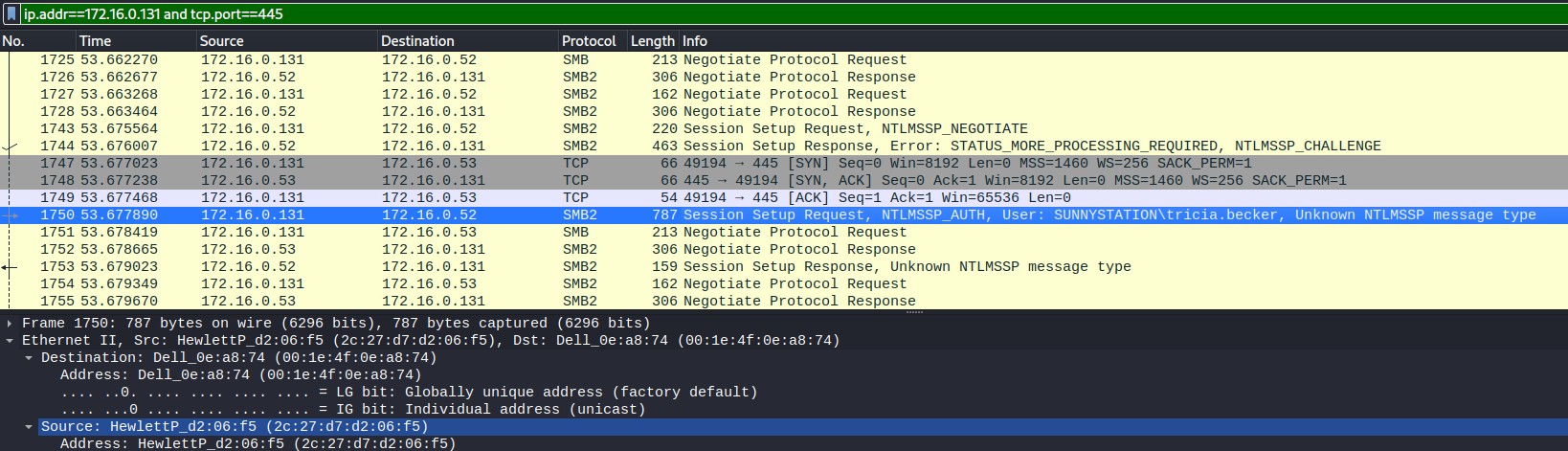
Figure 1.1.5 – Host: 172.16.0.131
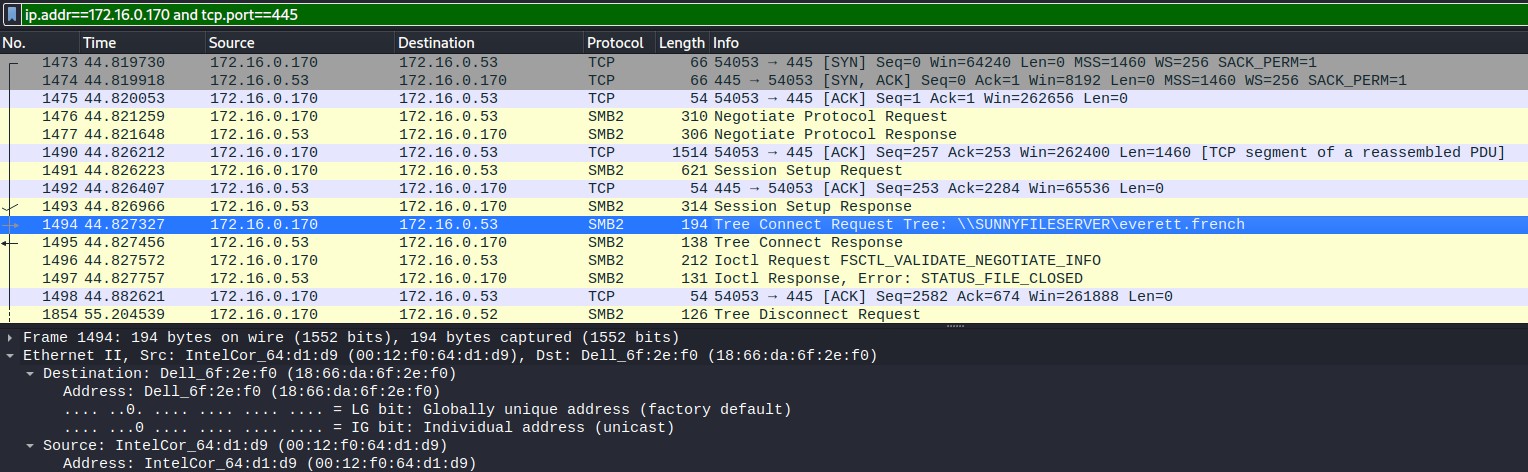
Figure 1.1.6 – Host: 172.16.0.170
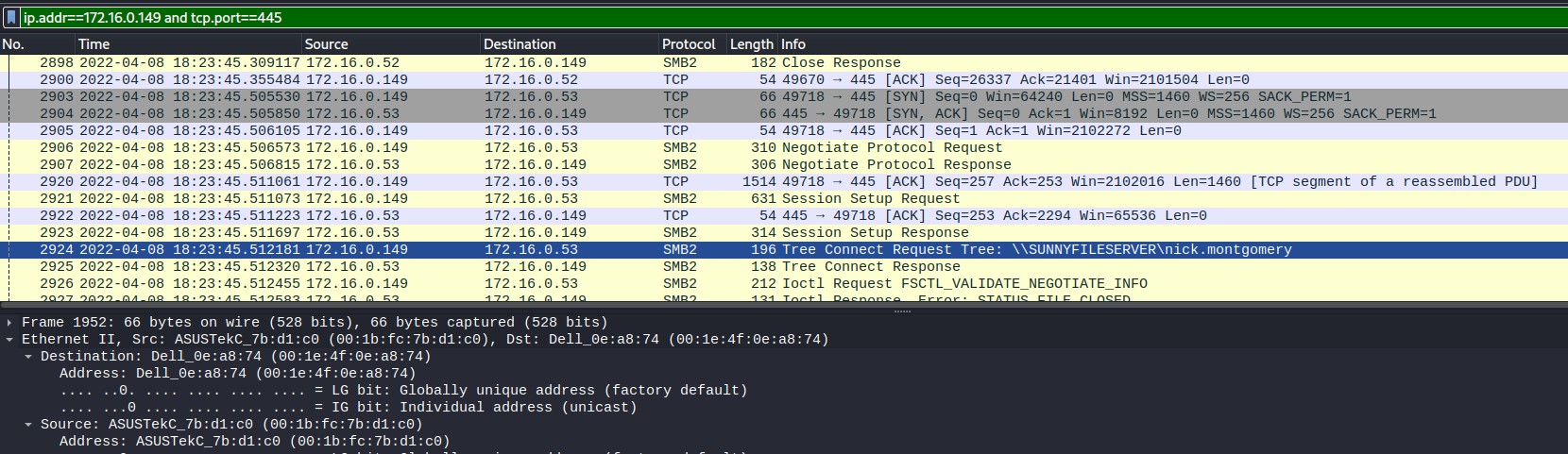
Figure 1.1.7 – Host: 172.16.0.149
Identified Malware
Host: 172.16.0.131
Filtering through HTTP traffic for this host, there are several connections to different domains, but all share a pattern. An encoded resource in a “uar3” file path. Researching the domain names links them to XLoader, formerly FormBook(Joe Sandbox). XLoader/Formbook is an infostealer, with its unique draw being that it can also operate on MacOS.
The domains matching this pattern also appear in an analysis of a FormBook infection, as well as several FormBook banlists. In addition, Brim identifies C&C traffic related to FormBook to IP addresses matching those used by XLoader/Formbook in the past.
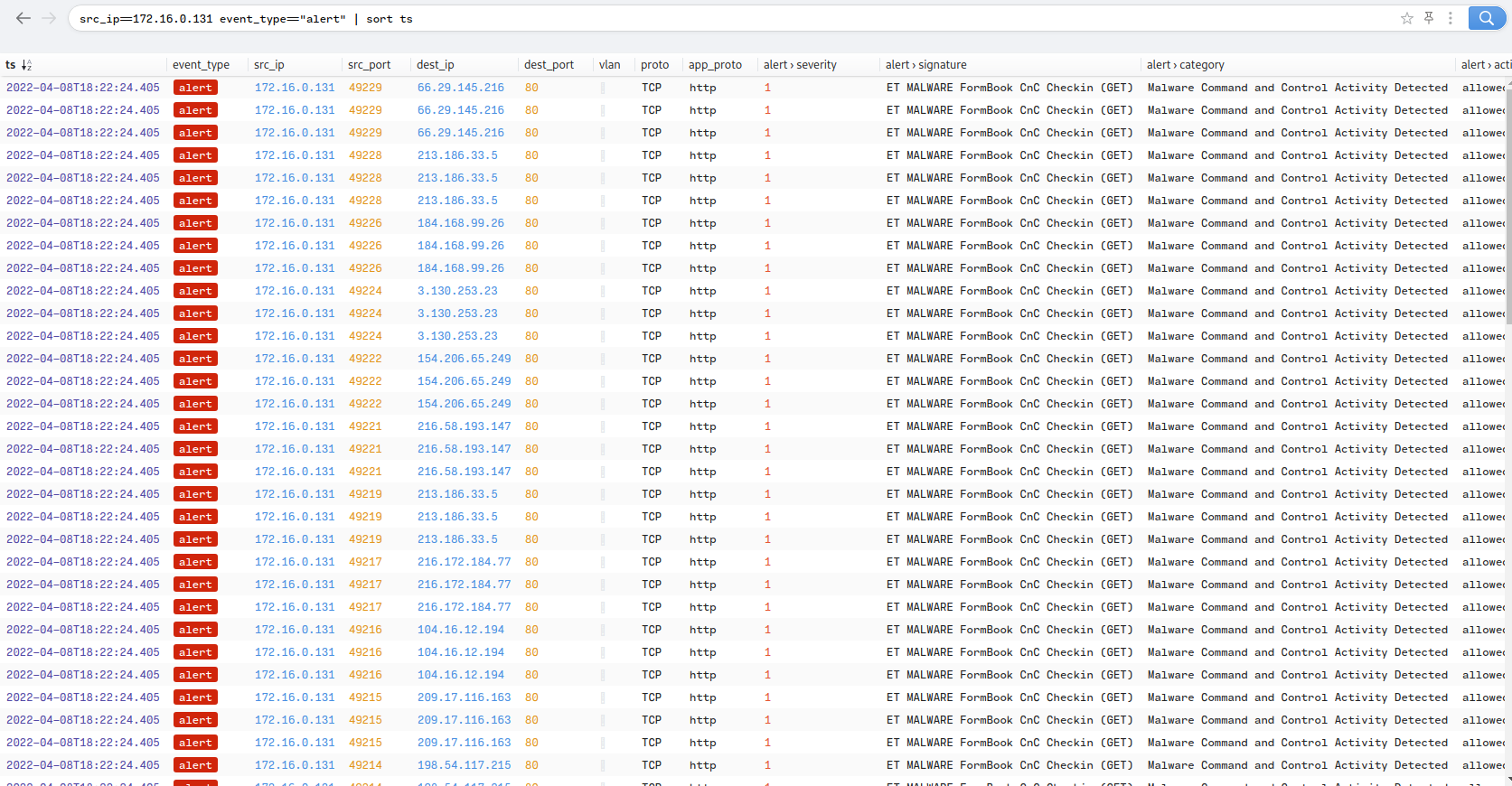
Figure 1.2.1 – FormBook C&C Traffic
Host: 172.16.0.170
On this host, some of the HTTP Traffic seemed obfuscated, as seen in Figure X. Digging into this and researching this IP, there were several connections to Dridex and Emotet malware in VirusTotal, as well as from malware researcher and reverse engineer reecDeep on twitter(reecDeep). URLhaus also shows a common theme in Dridex related domains to be related to IT systems, which is possibly related to the content of phishing emails used to deliver the malware (speculation only).
In addition, further in the traffic there was the domain dalgahavuzu.com. This domain was linked to Emotet and has been previously known to download DLLs. (URLhaus, n.d.)This seems a likely first infection stage, primarily due to the matches with the timestamps in the figures below, showing that first the DLL was downloaded, then the obfuscated traffic began. This activity hints at the obfuscated traffic being C&C traffic.
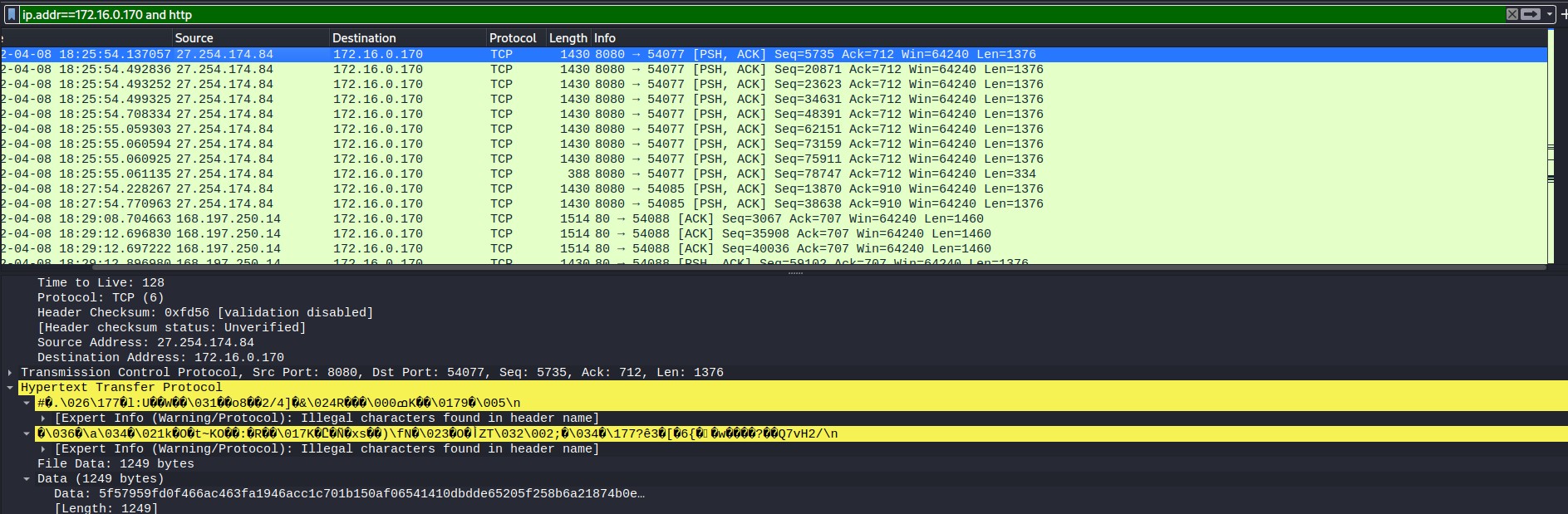
Figure 1.2.2 – Obfuscated Traffic
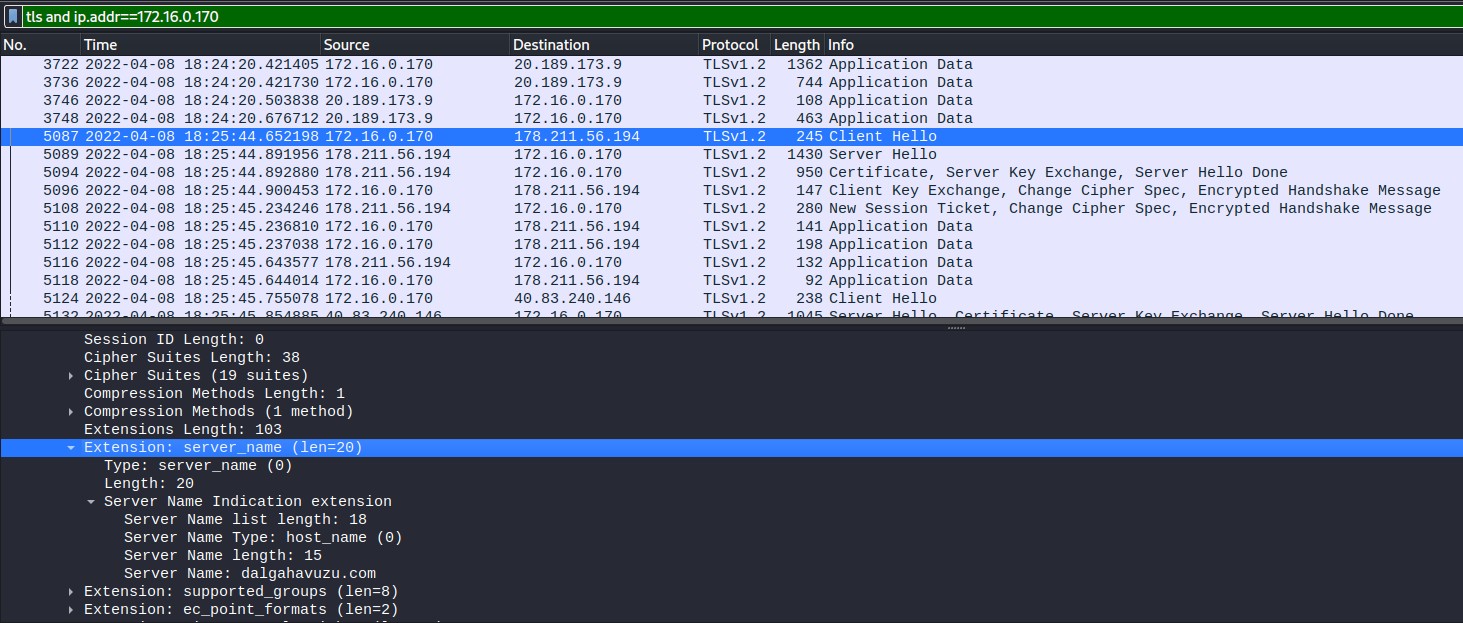
Figure 1.2.3 – DLL Associated Domain
Host 172.16.0.149
Unlike the previous host, here there is a captured packet showing the malware download. In the HTTP traffic on this host there is a DLL download in a HTTP GET request. The response code 200 indicates the file was successfully downloaded. The DLL name is a long string of characters, and the domain (ajaxmatters.com) is flagged in VirusTotal as a known infection source and phishing campaigns. This host also shows obfuscated HTTP traffic, similar to 170. This is also seemingly C&C traffic, hinting that the two infections are similar in nature. Both involve a DLL file download, and obfuscated C&C traffic.
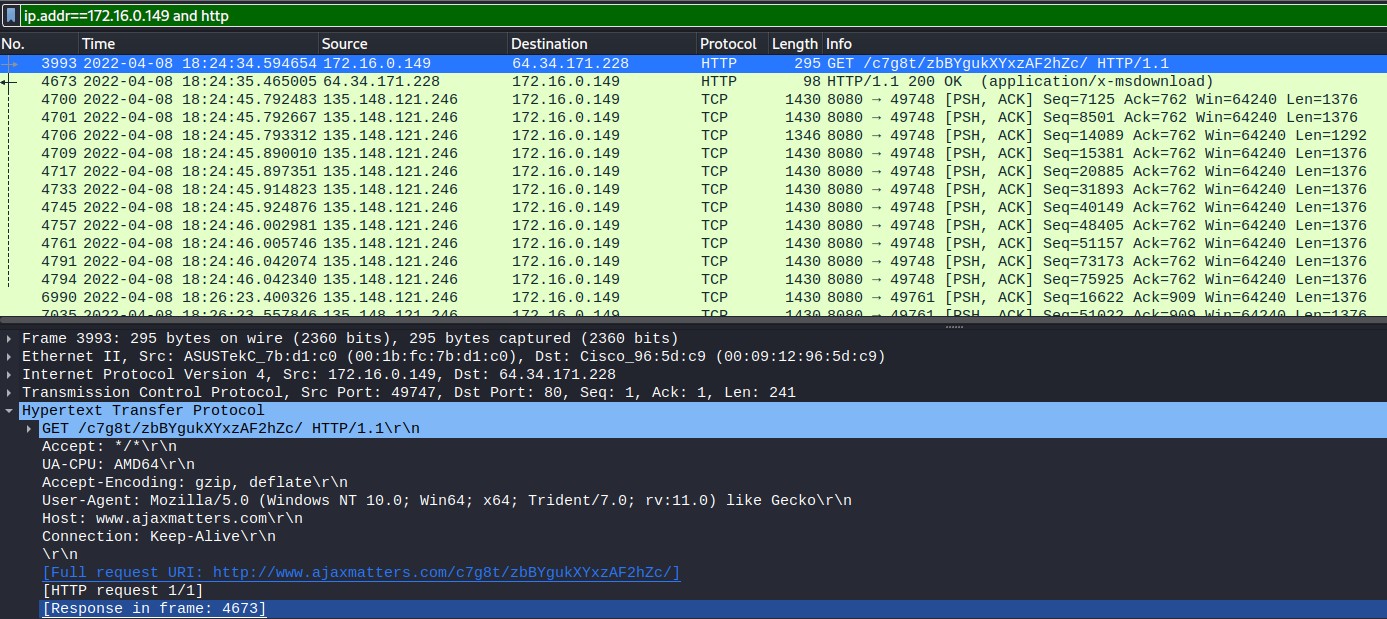
Figure 1.2.4 – DLL Download
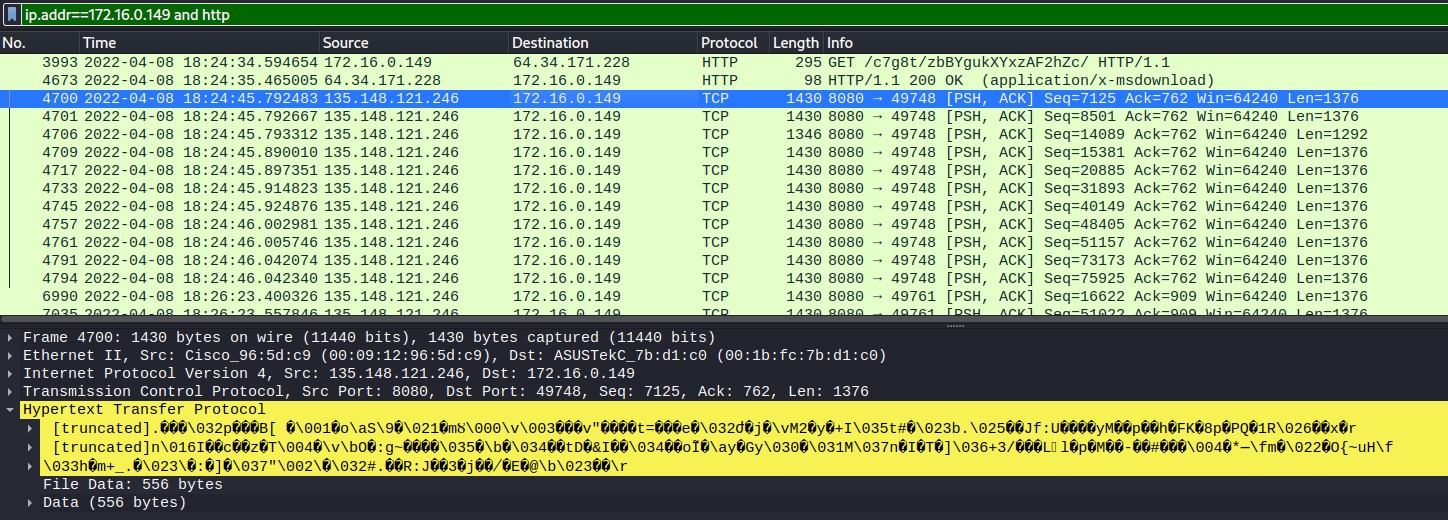
Figure 1.2.5 – Obfuscated Traffic
Malware
With the evidence gathered and presented previously, it seems conclusive enough to determine that all three hosts are infected with malware. The 172.16.0.131 host is infected with the info-stealer XLoader (Formerly FormBook). XLoader/FormBook is a sold for service malware that has been in the wild, for sale on hacking forums, since 2016. It uses keyloggers and form grabbers to steal the users information. Likely delivered using a phishing email.(Zhang, n.d.)
The hosts 172.16.0.149 and 172.16.0.170 are both infected with Emotet/Dridex, with the 149 host displaying spambot activity. The table below summarises the findings. While the evidence provided here only make clear connections to Emotet,
there is evidence that Dridex is the main malware on the 149 and 170 hosts. Evidence for this will be presented further into this report.
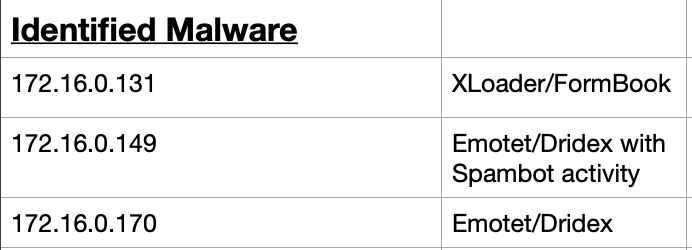
Figure 1.2.6 – Identified Malware
Malware Summary
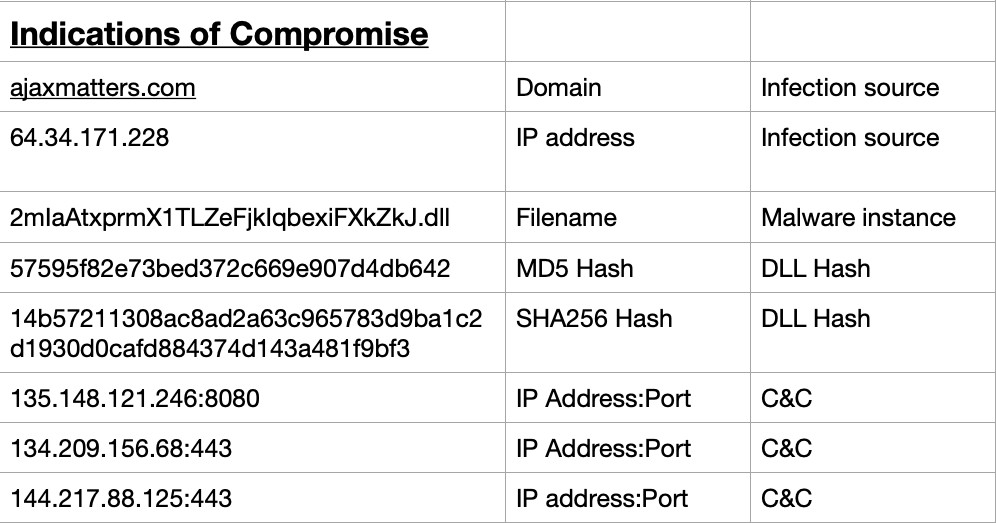
Figure 1.3.1 – IoC on Host 149
Emotet/Dridex – 172.16.0.149
The malware instance chosen to analyse in this report will be the Emotet/Dridex infection on host 172.16.0.149. This is done as everything covered in this analysis is relevant for the similar infection on the 170 host, but also covering the previously mentioned suspected spambot activity. The malware was downloaded from the
domain ajaxmatters.com, in the form of a DLL file at TS2022-04-08T18:24:35.465. The file name and MD5 hash is identified in the figure 1.3.2. The MD5 hash is identified by multiple security vendors as malicious, and linked to Emotet infections through VirusTotal.
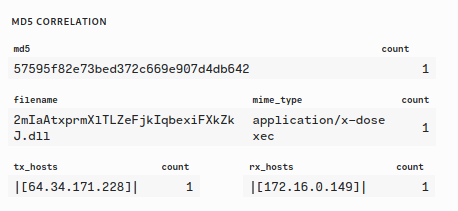
Figure 1.3.2 – DLL Filename and MD5 Hash
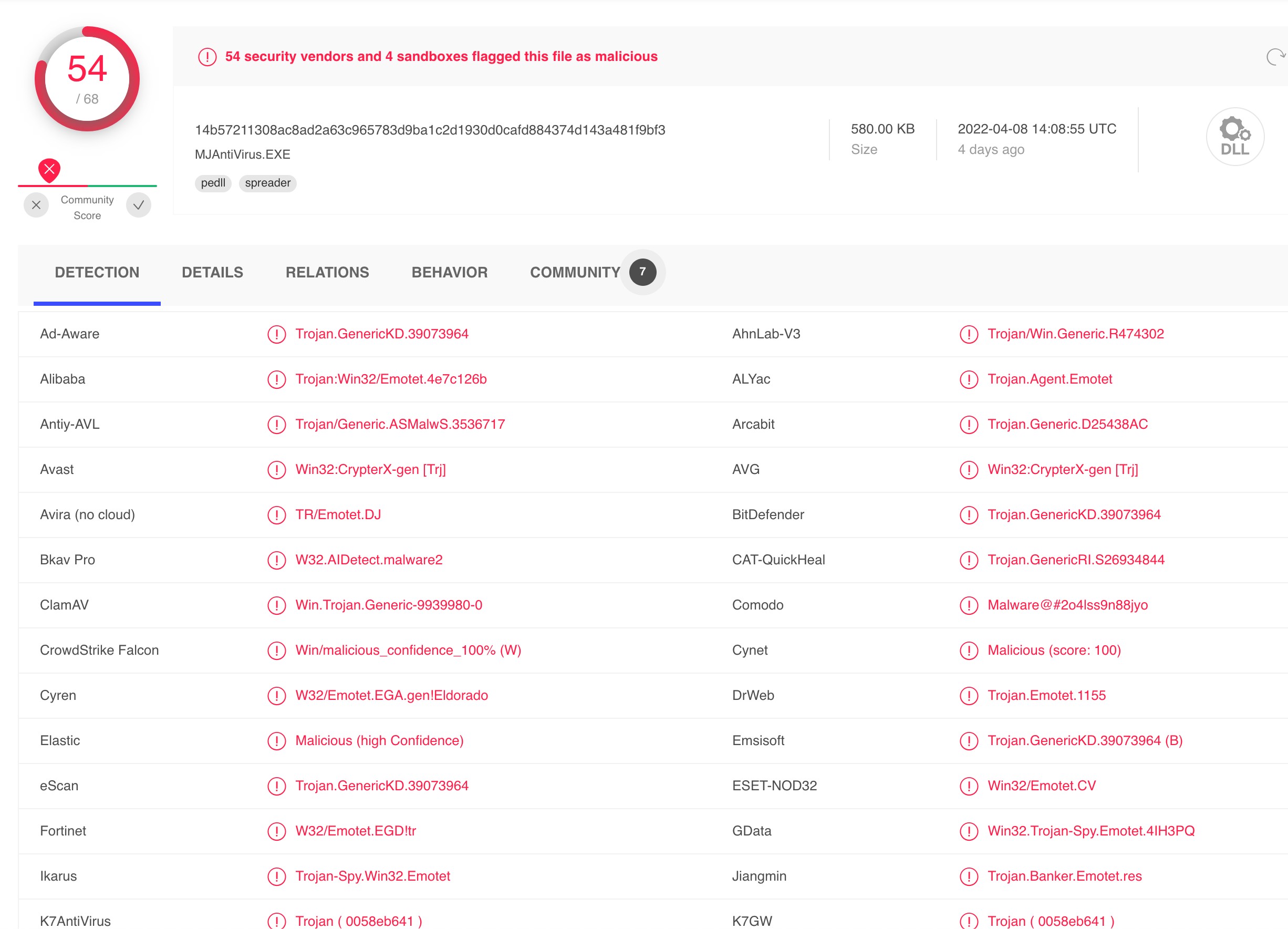
Figure 1.3.3 – VirusTotal on the MD5

Figure 1.3.4 – Brim identified C&C Traffic
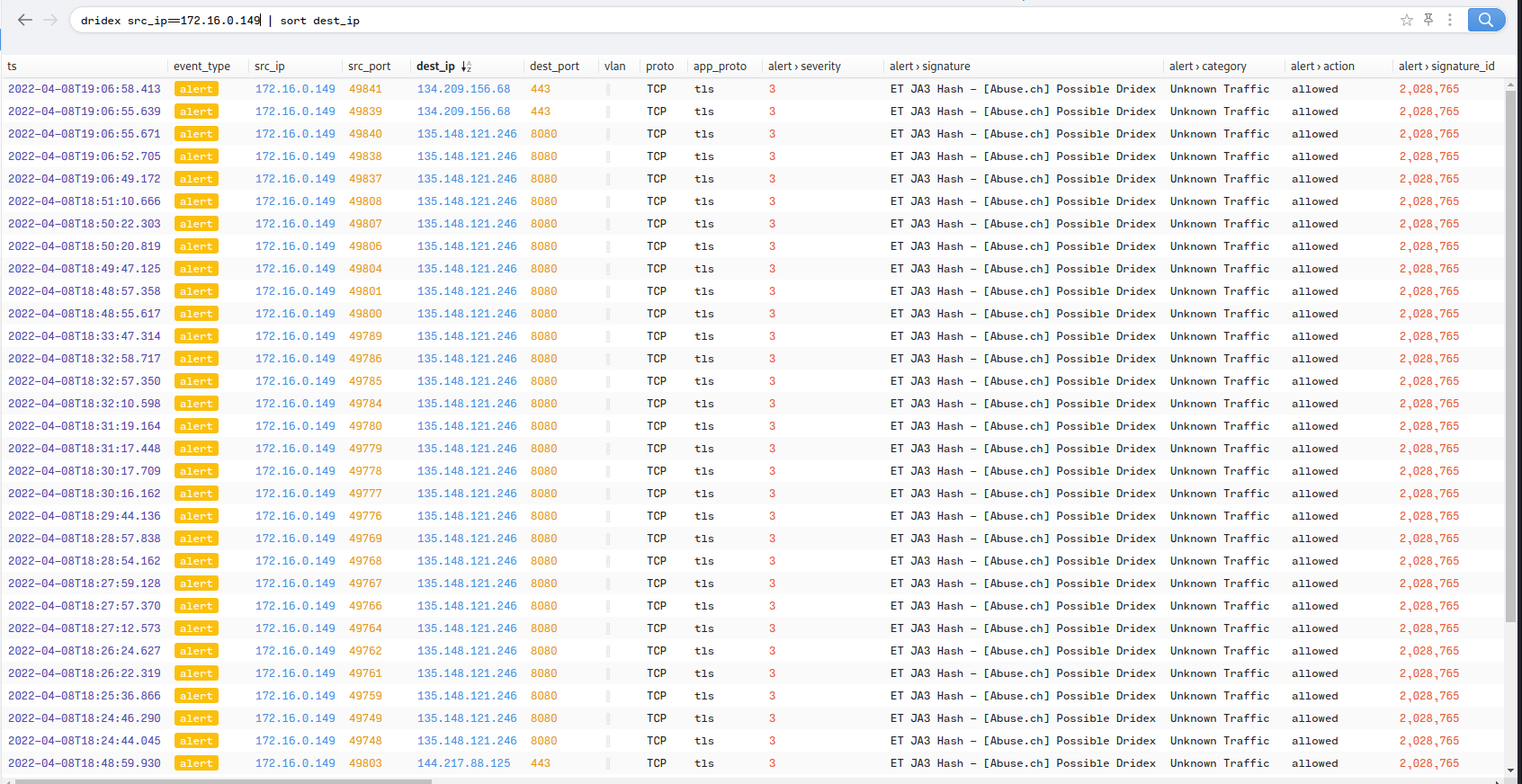
Figure 1.3.5 – HTTPS Traffic (Dridex)
C&C Traffic
With malware like Emotet, expectations would be to identify C&C traffic in HTTP POST requests that were seemingly missing from the capture file. One of the APT groups closely linked to the development of Emotet (Also known as Geodo) is the group known as MummySpider (Also known as TA542, Gold Crestwood)(Meyers, n.d.-a). Emotet was changed from another malware called Feodo to utilise an RSA key exchange for its C&C communication(Meyers, n.d.-b). Using Brim to filter for RSA key exchange on the packet reveals significant traffic. Crucially, this traffic is not seen on the 172.16.0.131 host, only on those suspected of Emotet infections. Figure 1.3.7 shows a screengrap of the display in Brim. This gives strong credence to this traffic being the Emotet C&C traffic that was seemingly missing. IP addresses found in this traffic is flagged as suspect in VirusTotal, and several of them have been previously known to communicate with files using suspect names, and flagged on VirusTotal as malicious.
Dridex
The MummySpider Emotet malware was advertised until 2015 when the group went private. Since then the malware is no longer used as a banking trojan, but as a loader, often delivering spambot plugins for self propagation and other malware like Dridex or Qakbot(Meyers, n.d.-b). Brim identifies volumes of traffic it flags as possible Dridex communication as shown in Figure 1.3.6, and the IP addresses in question are flagged as malicious in VirusTotal. This suggests the Dridex flagged traffic is the Dridex malwares own C&C traffic.
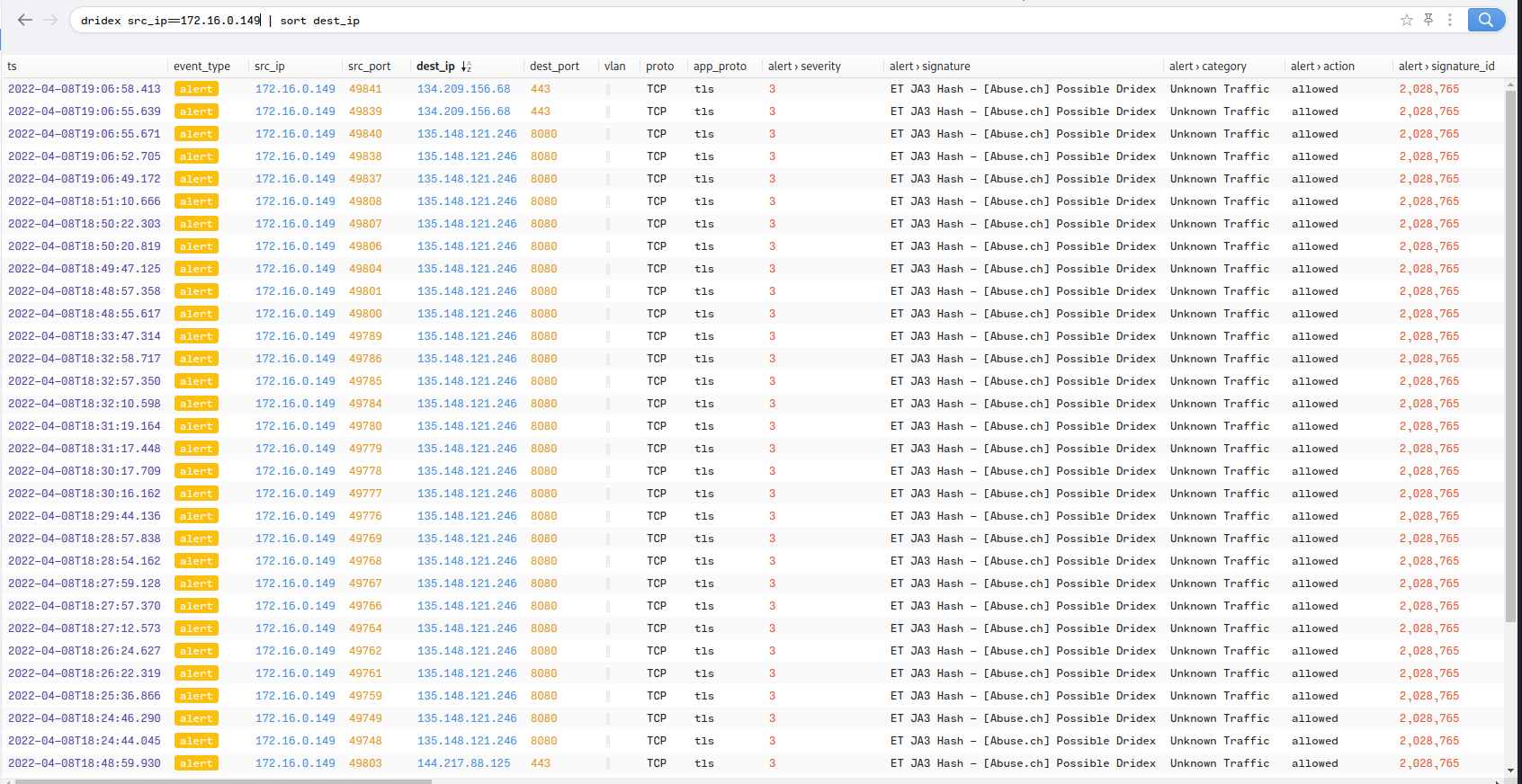
Figure 1.3.6 – Dridex Related Traffic
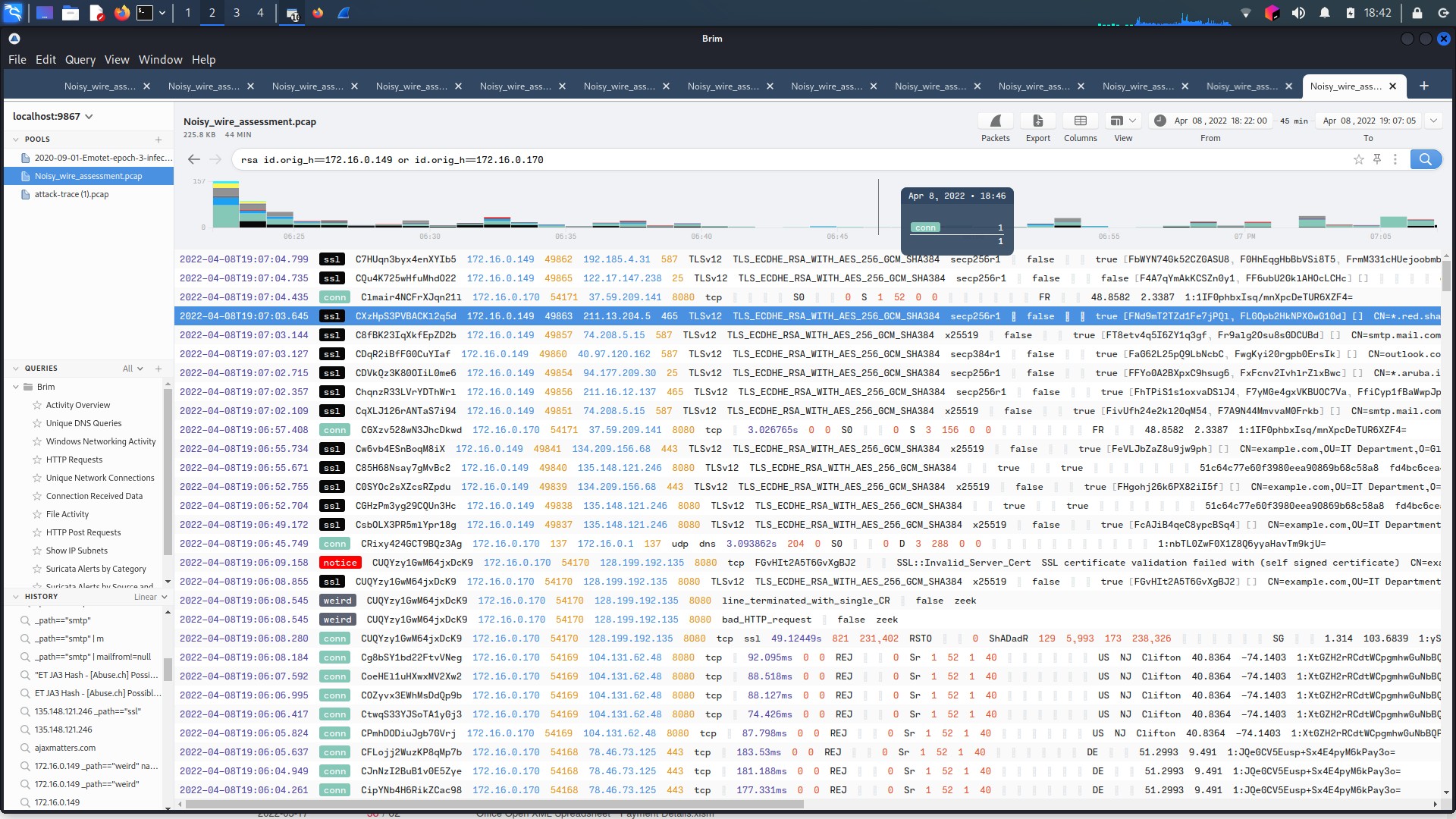
Figure 1.3.7 – RSA Filtered Traffic
This shows that the infected hosts were infected by Emotet, which then installed Dridex on the system. This matches MummySpider´s use of Emotet since 2015 and further hints at the groups involvement. Other versions of emotet would have shown Emotet as the sole malware on the system. This evidence is present on both the 170
and the 149 host. But unique to the 149 host is the presence of what seems to be spambot activity.
Spambot
MummySpider is known for using phishing emails to deliver their payloads. Filtering for mail activity, using “path==“smtp” – mailfrom!=null” in Brim reveals two outgoing emails sent from the infected host, both seemingly phishing attacks. Both emails were sent within 200 milliseconds of each other, heavily suggesting the presence of bot behaviour. One of these emails claims to be from kenmarefarmersunion.com, a North Dakotan oil company. The recipient, conniebanner28@yahoo.com and the associated IP is logged to a Indian Media company with no malicious flags. This is evidence that the communication is not extraction of data for the attacker, but propagation of a botnet.
Attached is a file named kenmarefarmersunion.com.xmls, perhaps masquerading as a domain and not the spreadsheet file it is. Emotet is known for spreading through xmls files, utilizing macros to install the malware on the victim.
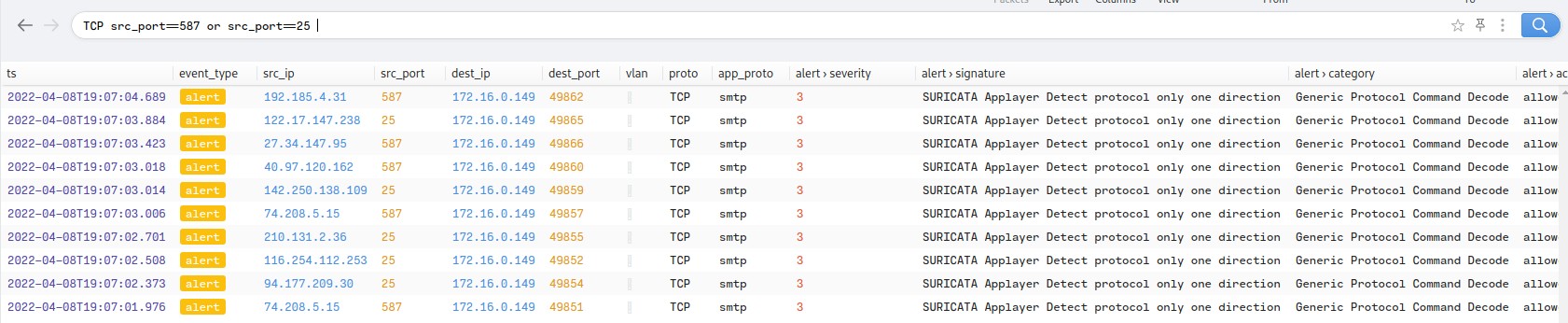
Figure 1.3.8 – Spambot activity
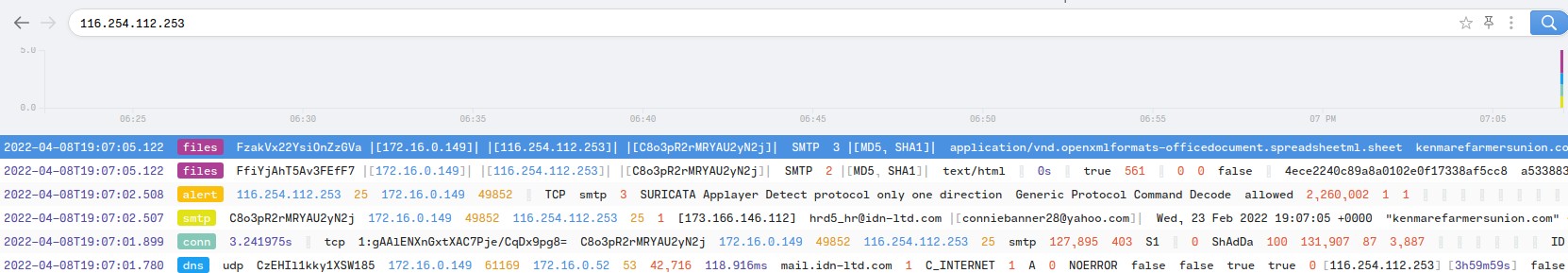
Figure 1.3.9 – Phishing Email Activity
Data Extraction
To round out the malware summary, there is also evidence of data extraction from the host. Usually data extraction is spotted by tracking files transferred from the infected host to a malicious server. This was not initially found, with the only outbound file of interest the spambot mail.
However, a technique found by security researcher Paul Melson, and described further by Sophos in 2018 might reveal the data extraction(Poston, n.d.)(SoCRadar, n.d.). The use of fake SSL certificates (or outdated ones in this case) allow for hidden data extraction. Data certificates are so widespread and common most detection methods might not pick it up. And when filtering for SSL certification traffic, what would you know there is plenty on the two machines infected with Emotet/Dridex. The third host, 172.16.0.131, has no SSL traffic to note. Also, when looking at data transfer, hands down the largest transfer of bytes is from the two infected hosts to IP addresses identified as malicious C&C servers (See figure 1.3.13).
All this put into consideration, this is very likely the stream used by the attackers to extract data from the infected host.
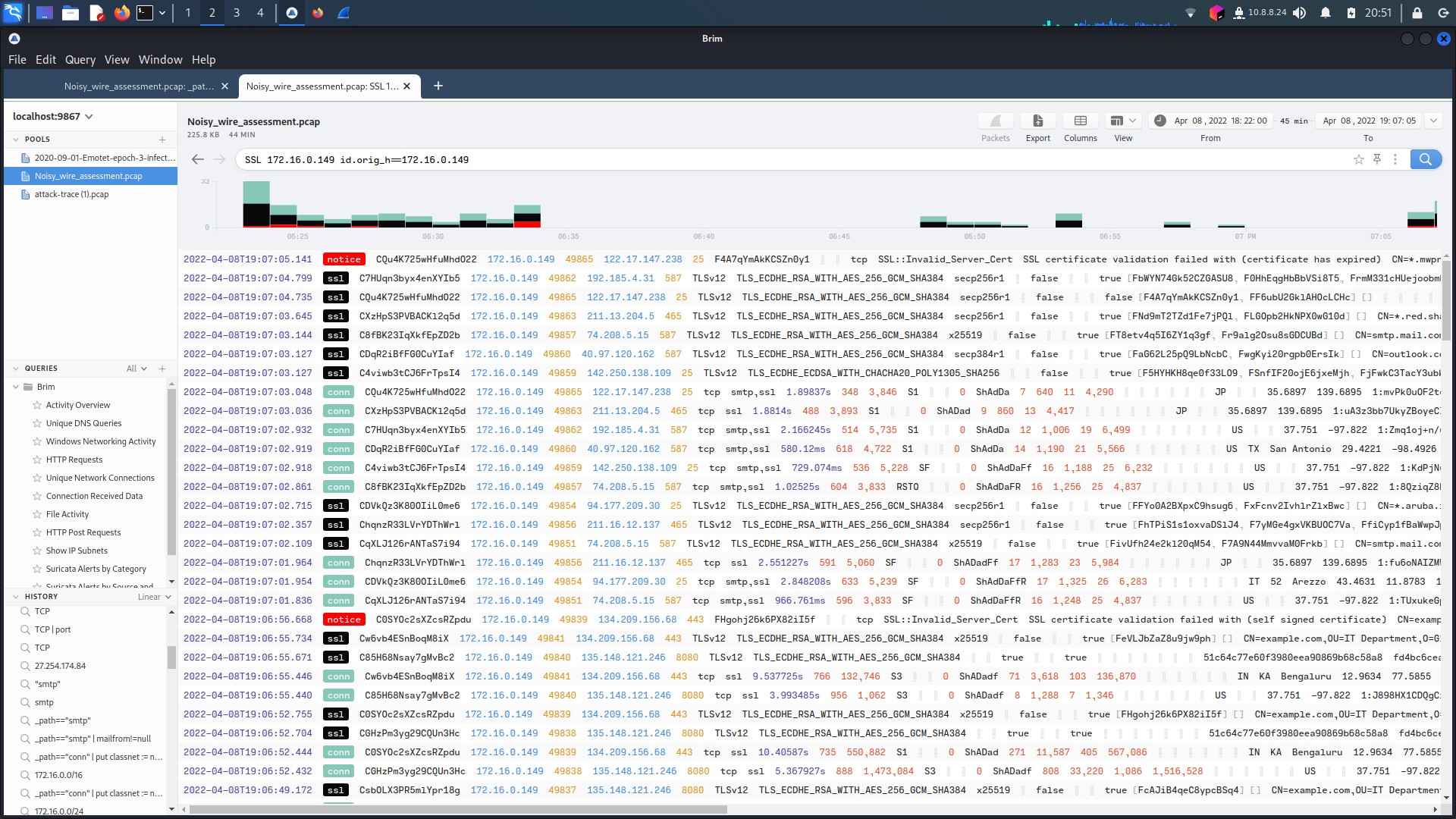
Figure 1.3.10 – Host 149 SSL Traffic
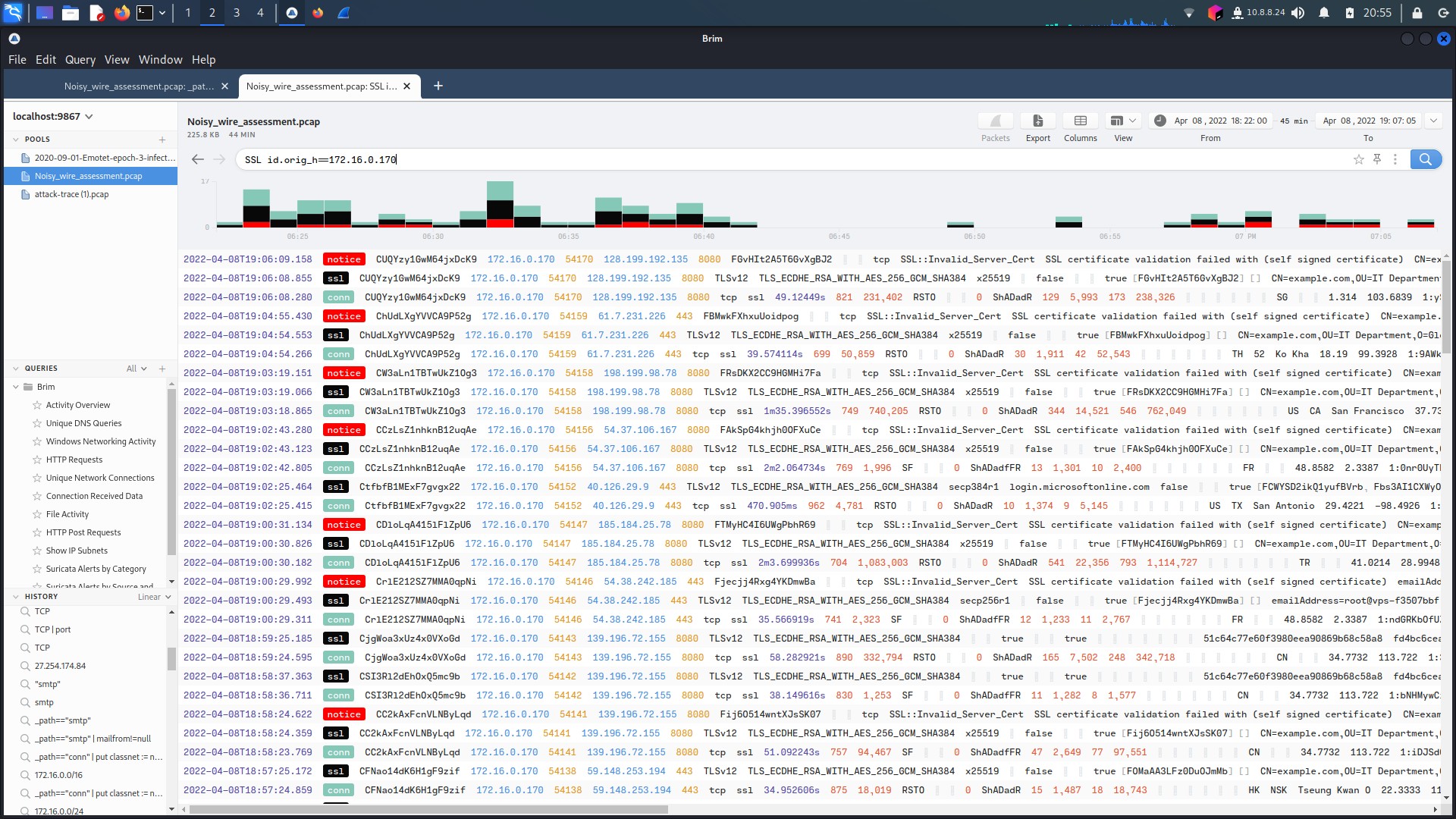
Figure 1.3.11 – Host 170 SSL Traffic
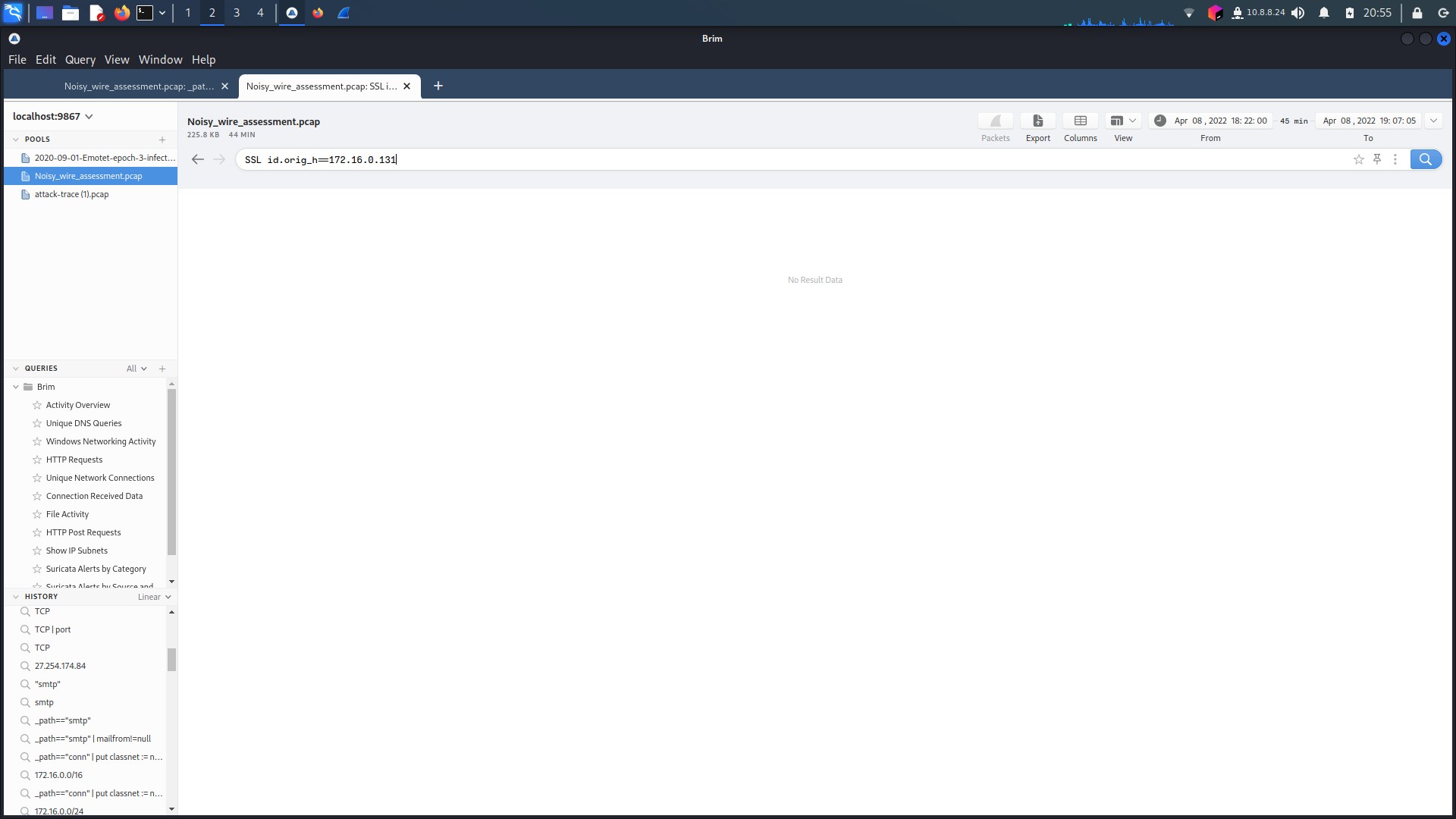
Figure 1.3.12 – Host 131 No SSL Traffic
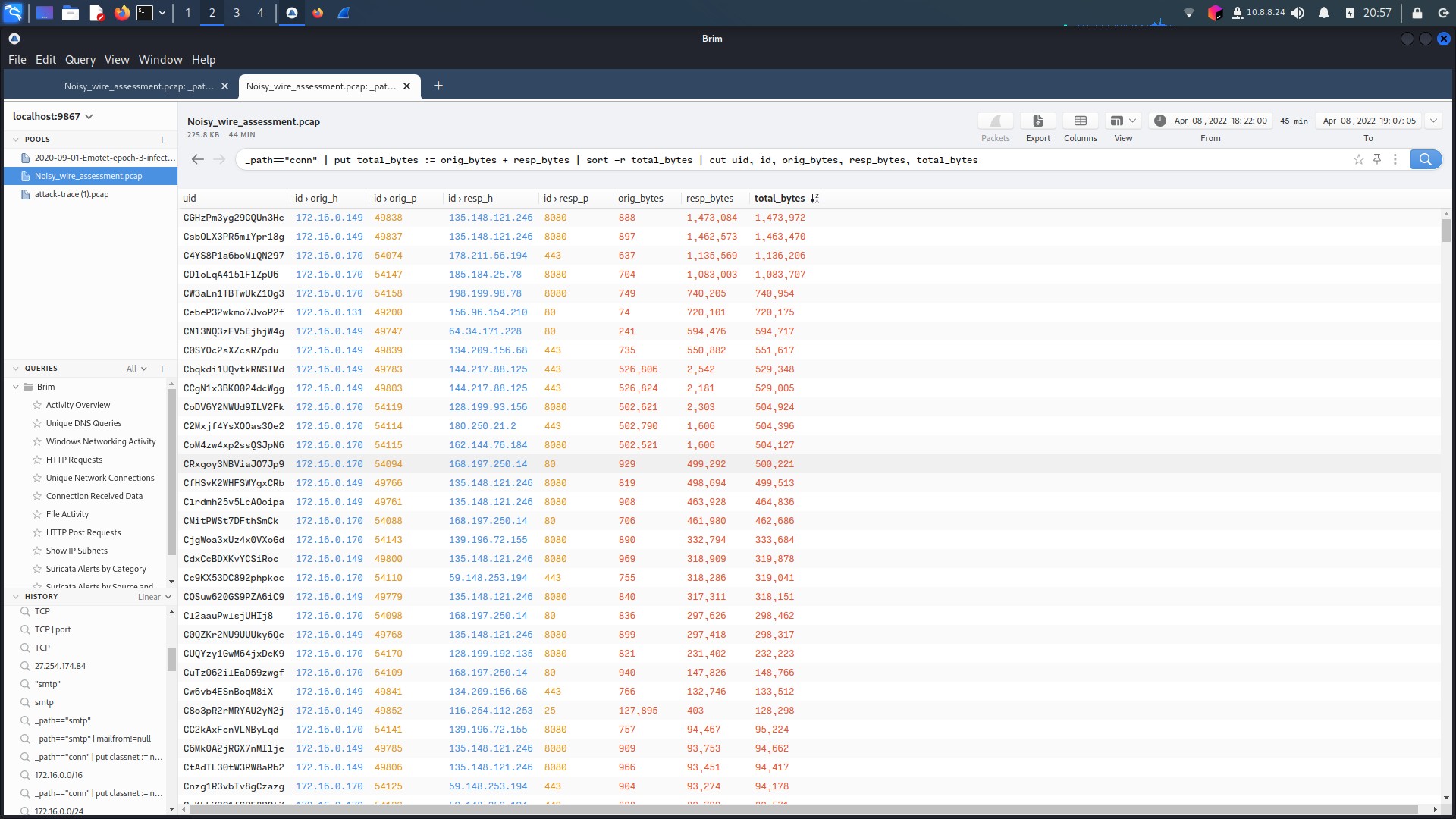
Figure 1.3.13 – Total Bytes
Attack Vectors
The malware DLL was downloaded from the malicious domain ajaxmatters.com. Ajax is a set of techniques for web development. Due to the domain used and the spambot activity on the infected host, it’s possible, but purely speculative, that the domain was delivered using phishing emails targeting IT personnel at SunnyStation. This is also in line with the traditional methods used by MummySpider, who seems to be the sole controller of Emotet as it stands.
Attribution
Attribtuion of cyber attacks and malware is very difficult to do confidently and with any degree of probability. Hence, much of this section is a combination of speculation, likelihood and educated guessing. Due to the presence of the RSA key exchange, a key trait of Emotet when compared to other banking trojans combined with the presence of Dridex malware on both infected systems and the presence of spambot activity on the 172.16.0.149 host, both of which are expected from
MummySpiders use of Emotet, the groups involvement seems likely. Adding to this the knowledge that the group no longer operates Emotet as a malware for sale and the malware seen here is not the older types of Emotet it seems plausible that the attacks can be safely attributed to the group MummySpider. The group is believed to operate out of Ukraine, and has been targeted by law enforcement multiple times.

Figure 1.5.1 – MummySpider
Full Traffic Analysis
Malware Activity
This sections aims to give an overview of the malwares presence on the host.
TS2022-04-08T18:23:49.512: Host requests new session
TS2022-04-08T18:24:34.594: Host sends HTTP GET request to ajaxmatters.com TS2022-04-08T18:24:35.465: Host successfully downloads malware DLL TS2022-04-08T18:24:44.045: Host sends first Emotet C&C traffic packet
TS2022-04-08T18:24:44.045: Host sends first Dridex C&C traffic packet Both these types of communication is done regularly (2-10 second intervals) TS2022-04-08T19:07:02.507: Host sends first suspected phishing mail TS2022-04-08T19:07:02.700: Host sends second mail, possible extraction
Methodology:
The analysis began with the mapping of the local network, as detailed in 1.1. This was primarily done using wireshark. First finding the Hosts, filtering with “udp.port==67” to see the three DHCP requests. Filtering with “ip.addr==ip address and tcp.port==445” to find the SMB2 packet (TS2022-04-08T18:23:18.083 for the 172.16.0.131 host as example) that the client requests access to the server with. These findings allows for identification of the relevant data used in 1.1.
From there, Wireshark was used to begin initial analysis by looking at the HTTP traffic of the hosts. This is where the first signs of malware were found, such as the previously mentioned DLL download for host 172.16.0.149 (TS2022-04- 08T18:24:35.465). Knowing the malwares present allows for the use of Brim and VirusTotal to begin identifying malicious IP´s and domains used in the attack.
From here, Brim was the main tool used, allowing for quicker and more powerful query combinations and an easier to visualise result set. It was with Brim most C&C traffic was identified, and crucially where the Dridex connection was made (Earliest: TS2022-04-08T18:24.44.045) and the spambot activity discovered (TS2022-04- 08T19:07:02.507). Used both through Brim and on its own, VirusTotal provided significant resources in identification for the report.
Tools:
For analysis of the capture file, the tools Brim and Wireshark were the primary tools used to analyse the network. VirusTotal, built into Brim, was used extensively to identify, log and track malicious IPs, domains and hashes discovered in the capture
file. The use of these tools is documented throughout the report where relevant. All analysis was done on Kali Linux.
Endpoint Reccomendations:
While the hosts 172.16.0.149 and 172.16.0.170 are both infected with Emotet/Dridex, there is no evidence hinting at cross host infection. Where this the case, there would be file transfers over smtp or similar protocols, an xmls or dll file for example. The hosts were seemingly infected independant of each other, perhaps using different versions of the malware. This is based on the presence of spambot activity on only one of the hosts.
For the specific malware instance present on 172.16.0.149 then this endpoint should be imaged and analysed. In addition the In addition, it’s important to track the phishing email and investigate its recipients endpoint if possible.
2.1 MITRE ATT&CK Heat-Map
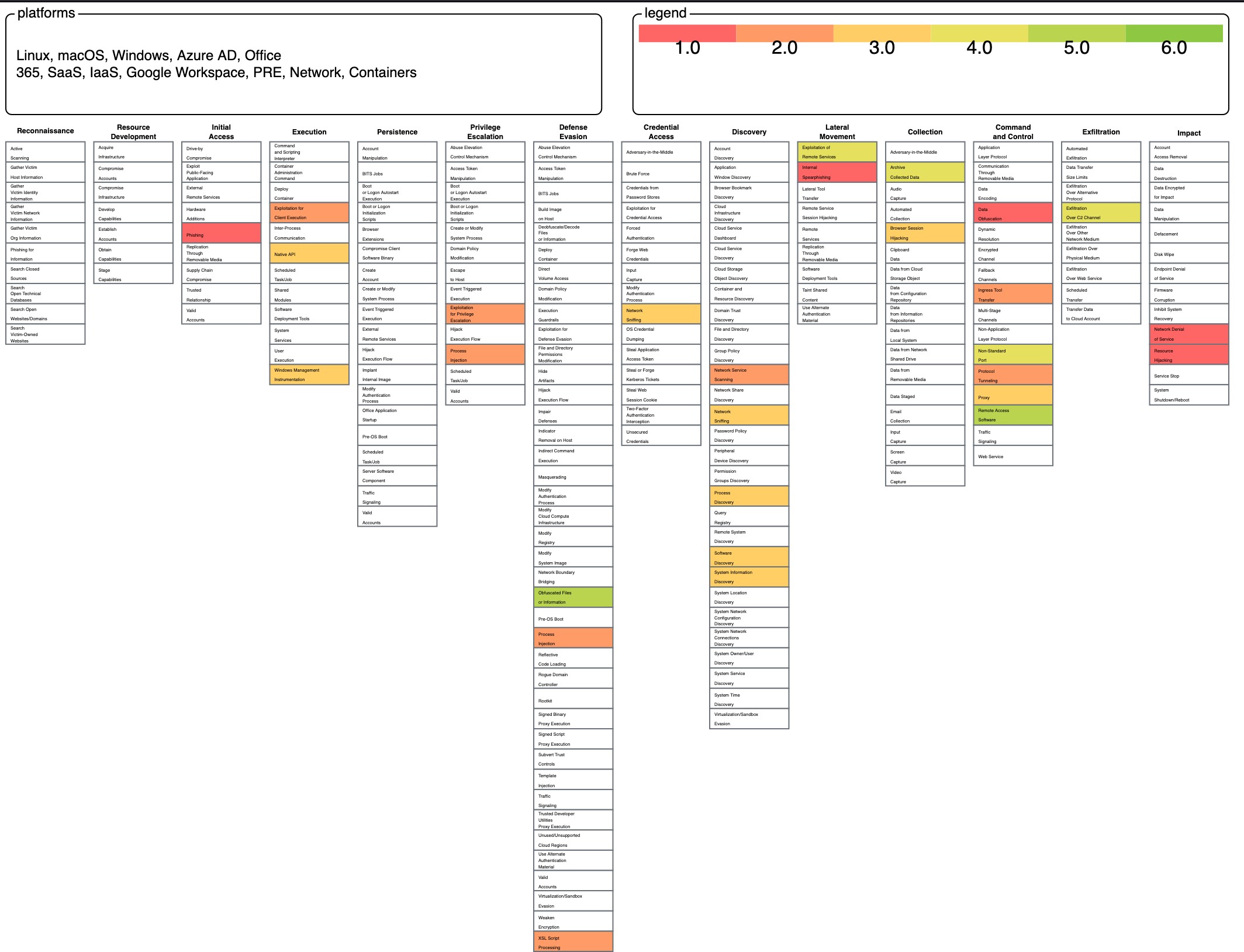
Figure 2.1.1 – MITRE ATT&CK Heat-Map
Legend:
1 = SunnyStation APT
2 = MummySpider/CobaltSpider
3 = Emotet
This is based on the current findings on the report, and there could be further relations to both Emotet and MummySpider, but this has not been uncovered as of the writing of this report.
Cyber Defence And Counter Measures
For the host 172.16.0.149, the main intrusion mechanic was through a malicious domain link, likely delivered by spearphishing. The weakest link in Cyber Security will always be human beings, but it is also the most versetaile solution. Phishing attack training seems an important start to bettering the defences at SunnyStation. In addition, most of the indicators of compromise found here are known actors, known malware and knows malicious links/domains/files.
An antivirus and other similar intrusion detection methods would be a second strong foundation. These are not costly changes, and would help bolster security significantly. In addition, better networking monitor software is needed, as most the malicious activity on the network has been flagged as suspicious and should have been blocked.
Communications with expired SSL certificates stand out the most as a clear point of pain. The company should revise its networking rules and find and implement tools that are capable of tracking and blocking malicious traffic. This will naturally not block 0 day exploits, but nothing seen in the capture file indicates 0 days or that level of advanced malware. These were basic and at this point standard malware delivered through traditional means. Basic cyber defence would have hindered these intrusions.
Executive Summary
SunnyStation had noticed network degradation in the form of latency and bandwidth usage as well as general system degradation in the form of slowed machines. This report was commissioned to analyse and track possible malware and APT presence on the network.
This analysis revealed several indications of compromise on all three hosts. The first host was infected with an info-stealer known as Xloader (formerly FormBook)
while the other two hosts were infected with a Emotet/Dridex combination of malware. The report made a more detailed dive into the Emotet/Dridex infection on host 172.16.0.149, due to it also showing signs of spambot behaviour and presented the greater threat. The report went on to create a MITRE ATT&CK heat- map with the intent to attribute the incursion to the APT group known as MummySpider, as well as showing the infectious malware to in fact be Emotet/Dridex. In addition the report drafted some high level ideas for increased defence and counter measures to inhibit future attacks.
The main points of this is for SunnyStation to follow up the report with an installation of an antivirus software, training for personnel in anti phishing and malware identification and further locking down the network for unneeded/unsafe traffic.
Sources:
Joe Sandbox. (n.d.). Joe Sandbox – Analysis. Retrieved April 13, 2022, from https://www.joesandbox.com/analysis/574776/0/html
Meyers, A. (n.d.-a). MummySpider – Crowdstrike. Retrieved April 13, 2022, from https://www.crowdstrike.com/blog/meet-crowdstrikes-adversary-of-the- month-for-february-mummy-spider/
Meyers, A. (n.d.-b). MummySpider – Crowdstrike. Retrieved April 13, 2022, from https://malpedia.caad.fkie.fraunhofer.de/
Poston, H. (n.d.). aeb4dd59eda23a701d3563b7e240b5da74f03240 @ resources.infosecinstitute.com. Retrieved April 13, 2022, from https://resources.infosecinstitute.com/topic/hiding-malware-in-certificates/
reecDeep. (n.d.). Tweet – Dridex. Retrieved April 13, 2022, from https://twitter.com/reecdeep/status/1335923885812879360
SoCRadar. (n.d.). How Expired Digital Certificates Can Be a Nightmare? Retrieved April 13, 2022, from https://socradar.io/how-expired-digital-certificates-can- be-a-nightmare-2/
URLhaus. (n.d.). URLhaus – dalgahavuzu.com. Retrieved April 13, 2022, from https://urlhaus.abuse.ch/url/2055472/
Zhang, X. (n.d.). Deep Analysis – New Formbook variant. Retrieved April 13, 2022, from https://www.fortinet.com/blog/threat-research/deep-analysis-new- formbook-variant-delivered-phishing-campaign-part-I

Leave a Reply